¶ Preamble/Introduction
Garuda Linux provides optional SecureBoot support for either compatibility reasons or increased security.
The following list will explain when SecureBoot support is useful/necessary:
- If a potential increase in security is desired.
SecureBoot does not protect against physical access based attacks. An attacker can enroll their own key (or disable SecureBoot). There is no bulletproof way to protect against physical attacks. Full disk encryption should be used to protect against the most common threat: Data extracted from physically stolen devices.
The private MOK (key) is stored on the disk and accessible at
/var/lib/garuda/secureboot/keys/. Additionally, the Arch Linux kernels do not currently enforce very strict SecureBoot rules. The effectiveness of SecureBoot on Garuda Linux as a security measure is therefore limited.
Allowing SecureBoot to be enabled will allow other installed operating systems with full vendor-only (no MOK on the disk) SecureBoot support (for example Microsoft Windows, Ubuntu, Debian, etc. as long as no MOK is enrolled (commonly used for custom kernel modules)) to benefit from SecureBoot.
- Another operating system or software on another operating system requires SecureBoot (prime use-case).
- An alternative is to toggle SecureBoot whenever using this software (not desirable).
For any other use case, we recommend leaving SecureBoot disabled.
SecureBoot support cannot be enabled on legacy/BIOS systems. Only UEFI is supported.
¶ Setup
¶ Installing SecureBoot support
Install garuda-secureboot
sudo pacman -S garuda-secureboot
Install SecureBoot support:
sudo garuda-secureboot --install
Expected output:
:: Creating signing keys...
:: Asking Garuda tooling to reinstall and sign GRUB...
:: Asking Garuda tooling to reinstall and sign kernels...
:: Updating UEFI boot entries...
:: Installing shim bootloader...
:: SecureBoot support has been enabled. Reboot, enable secureboot in the system firmware settings and complete the MOK enrollment to finalize the process.
¶ Configuring Shim
Reboot the system and press any key when seeing this screen:
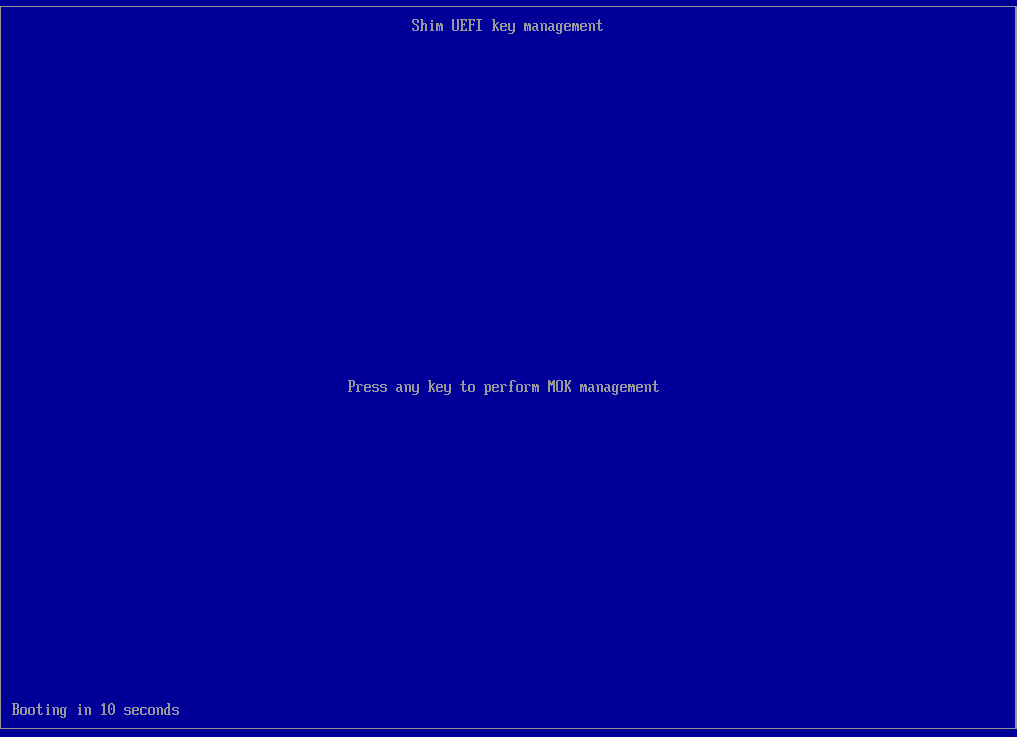
Select “Enroll MOK”:
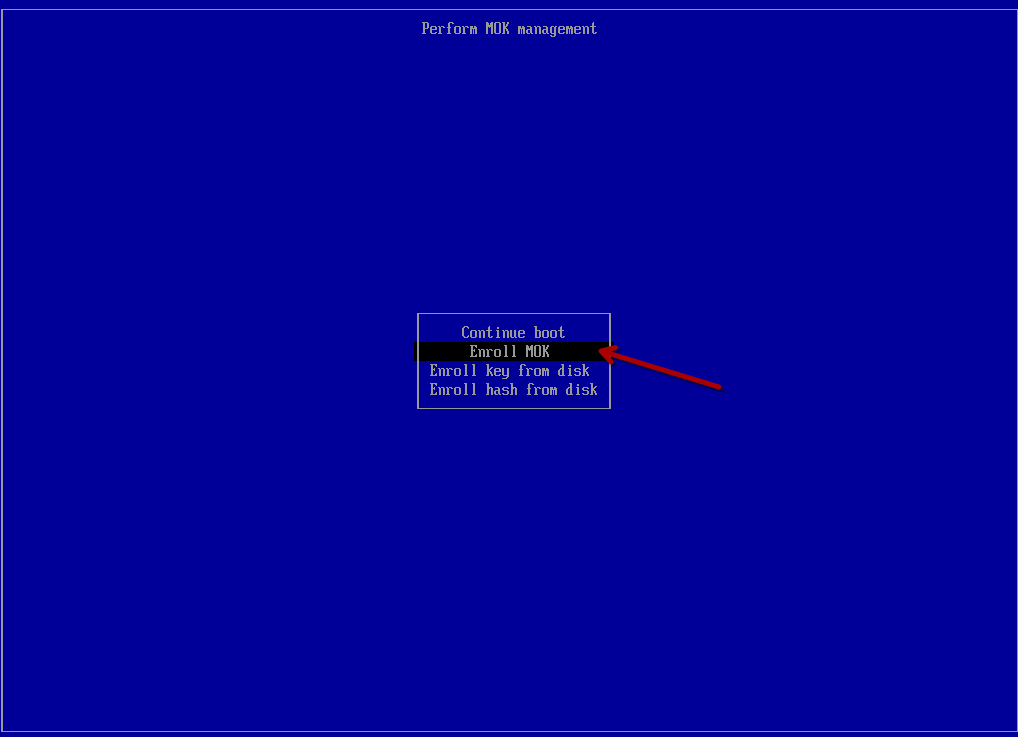
Select “Continue”
Select “Yes”
Enter the password garuda (all lowercase). The password will be invisible in the password box. Press “Enter” when done.
Select “Reboot”.
¶ Enabling SecureBoot
Boot into BIOS/UEFI Setup and enable SecureBoot. It may be necessary to “reset the keys” to default to exit “Setup mode”.
Upon rebooting the system, SecureBoot should be enabled:
$ sudo garuda-secureboot
SecureBoot support is active.
SecureBoot is enabled.
¶ Maintenance
The “Garuda” bootloader is the only bootloader that will be automatically managed for SecureBoot support: Why should the “Garuda” bootloader be used?.
Linux kernels will be automatically signed when installed via garuda-dracut-support. The command dracut-rebuild can be used to manually reinstall the kernels if necessary.
The GRUB bootloader will be automatically signed when installed via garuda-hooks. If needed, reinstalling GRUB can be done via sudo pacman -S grub, which will trigger the pacman hook for automatic GRUB updates.
Secureboot keys/certificates can be found at /var/lib/garuda/secureboot/keys/ if manual signing is necessary.
¶ Uninstalling
Before continuing, disable SecureBoot in the BIOS/UEFI Setup.
Remove SecureBoot support:
sudo garuda-secureboot --uninstall
Expected output:
:: Updating UEFI boot entries...
:: Uninstalling shim bootloader...
:: Asking Garuda tooling to reinstall GRUB...
:: Asking Garuda tooling to reinstall kernels...
:: Removing signing keys...
:: SecureBoot support has been disabled.